- Real Dns 6 6 2 – Dynamic Dns Update Client
- Real Dns 6 6 2 – Dynamic Dns Update Client Duc For Windows
- Real Dns 6 6 2 – Dynamic Dns Update Client Linux
- Dynamic DNS providers allow a minimum update time of 10 minutes if the IP is the same as the last one. If you execute more updates on the same hostname with the same IP under 10 minutes then the dynamic DNS provider can block your hostname. For this reason RealDNS first checks if the IP is changed and then sends the update request.
- The best dynamic DNS update client on App Store. Also available on macOS X, with iCloud synchronization and Apple Watch. RealDNS Mobile updates 18 dynamic DNS providers: Dyn, NoIP, FreeDNS, ChangeIP, DuckDNS, XpertDNS, Strato, DynDNS.it, DtDNS, EasyDNS, DNS Made Easy, CloudFlare, Google Domains, Na.
- Our Dynamic DNS service gives you an easy to remember hostname i.e. Yourname.noip.me, (just like when you assign 'Joe' to his phone number in your phone) you run a small piece of software on your computer or device you would like to access remotely, and whenever your IP address changes, we update your hostname to reflect that change.
Translation(s): none
This is a Python3 client for DNSEXIT dynamic dns service. It is an (almost) faithful replica of the Perl original package for Linux available at ipUpdate-1.71.tar.gz. The setup.py script generates dnsexit.conf configuration file (100% compatible with the Perl version) in /etc and enables a system service if requested.
Contents
- How to set up DDNS
DDNS — Dynamic DNS Airserver 7 1 4 mac torrent.
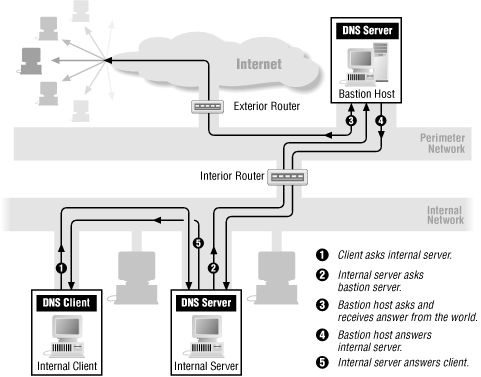
DDNS is a service that can be used to automatically update DNS records if client PCs get their IP settings from a DHCP Server. These updates are usually performed by the DHCP Server. DDNS is handy if you have a DNS Server in your local network that should be able to resolve the names of your local PCs. This information should not be forwarded to outside your network, unless you use public IP addresses.
In this example configuration I use private IP addresses and therefore configure the DNS Server to not forward this information to a public DNS Server. Although, in case your set up requires it to forward this information, I'll describe also this case at the appropriate point.
You should already have a working DHCP and DNS server set up before following the below instructions. You can find information on how to do that at DHCP_Server and Bind9.
Generate a key for verification
We have to create a key, that will be used to secure the exchange of information between DHCP and DNS server. Only our DHCP server should be allowed to perform DNS record updates, not just anyone.
Generate the key
This will create two files, Kdhcp_updater.*.key and Kdhcp_updater.*.private. Copy the key from the *.private file (the line with the key should look similar to this one: https://torrentspin.mystrikingly.com/blog/teamviewer-web-online.
Everything after 'Key: ' is the actual key.
Create the file ddns.key

Everything after 'Key: ' is the actual key.
Create the file ddns.key
Now create a new file (ddns.key) with the following content (don't forget to replace with your key):
in my case it would look like this:
Copy the key into the correct locations
Copy this file to /etc/bind/ and /etc/dhcp and adjust the file permissions as follows:
or in two lines:
DNS Server Configuration
Configure zones to be updated
The DNS server must be configured to allow updates for each zone that the DHCP server will be updating. In our example the clients in the example.org domain will be assigned addresses on the 192.168.2.0/24 subnet. We will need a key declaration for our key, and two zone declarations - one for the forward lookup zone and one for the reverse lookup zone. To do so add the following to the file /etc/bind/named.conf.local:
The option notify no stops named (the DNS daemon) from forwarding information about the local network to external DNS servers. This is only useful if you use private addresses in your network. In case you use public addresses, you want your DNS to forward that information to public DNS servers. To configure this, just delete the line notify no;.
Create the zone files
Then you have to create two zone files, one for the forward lookup zone (db.example.org) and one for the reverse lookup zone (db.192.168.2). These are the zones you defined previously in the file /etc/bind/named.conf.local.
You can copy the sample file db.empty and then just add your changes.
The following listing shows the contents of db.empty, which is (after the previous step) the same as db.example.org and db.192.168.2.
So let's first edit db.example.org. It should afterwards look like this:
and then db.192.168.2:
The trailing dot is important, because it makes the name a FQDN (Fully Qualified Domain Name). In this case the nameserver's IP address is 192.168.2.1 and it's name is ns. Adjust the files according to your network's configuration.
Create symbolic links
Finally we need to create links from /var/cache/bind to the actual zone files in /etc/bind. Loopback 1.0.1 %2b core keygen for macos. This is because /etc/bind is not writeable for bind, but /var/cache/bind is.
Be careful about the permissions of the directory that contains these links. The user/group bind should be able to write to it. If the permissions are like in the following listing, it should be ok.
DHCP Server Configuration
Additionally you have to configure your DHCP server to update these zones. To do so, you need to edit the file /etc/dhcp/dhcpd.conf. This file consists of different sections. In the global section, which is everything that is not inside a Subnet-, or group block, you have to add the following:
option domain-name
This options specifies the domain name, which is also used for DDNS.
ddns-update-style
This option should always be interim. The only other option is adhoc, but that one is outdated .
client-updates
If you use the option allow client-updates, the clients are allowed to register their name at the DNS server by themselves. We don't want this, so I added ignore client-updates (which is already the default option), just to show this explicitly.
update-static-leases
By default the DHCP-Server doesn't update the DNS entries of static leases. If you want it to update them, you need to set this option to on. It can be that this causes some problems, that's why the manpage of dhcpd.conf doesn't recommend the use of it. If you experience problems, turn it off, but then you have to configure these hosts statically not only for DHCP, but also for DNS.
You have to add the following lines for the zones that shall be updated by your DHCP server.
The primary statement specifies the IP address of the name server whose zone information is to be updated. In this case DHCP and DNS server are running on the same machine, that's why we put 127.0.0.1 there. If that's not the case, you have to put the IP address of the machine that the DNS server is running on there. The zone descriptions have to end with a period.
The complete dhcpd.conf file after the previous steps and with a basic configuration for the subnet 192.168.2.0/24:
Restart the servers
Test it
Now that everything is set up it's time to test it.
The easiest way to do so, is to connect a PC to your network and then check /var/log/syslog at the server. You can do so by issuing the following command:
If everything works fine, you should find something similar to the following lines in this command's output:
If not, you might want to do your on research on the Internet and if you find a solution, you might want to add information about it to this document.
Another way to test it
Go to your client computers and enable them to take an IP from a DHCP server. With the following command check if your client computer name is updated in DNS. It will resolve your name with the newly allocated IP.
Good Luck with your newly created Dynamic DNS Server.
See Bind9 and DHCP_Server for more information on DNS and DHCP.
Julien Valroff wrote a great article about a DDNS setup similar to services like DynDNS.org or Zonedit.com. You can find it here.
Here are some external resources which will allow you to study the DDNS methods in detail:
https://www.isc.org/software/bind - ISC BIND homepage
https://www.isc.org/software/dhcp - ISC DHCP homepage
https://web.archive.org/web/20020421014410/http://www.oceanwave.com/technical-resources/unix-admin/nsupdate.html - A DDNS Server Using BIND and Nsupdate
http://web.archive.org/web/20120130200400/http://ops.ietf.org/dns/dynupd/secure-ddns-howto.html - Secure dynamic DNS howto
http://dag.wieers.com/howto/bits/bind-ddns.php - Bind Dynamic DNS (DDNS) updates using nsupdate
https://web.archive.org/web/20180831164247/http://linux.yyz.us/nsupdate/ - nsupdate: Painless Dynamic DNS
DNS:
Real Dns 6 6 2 – Dynamic Dns Update Client
http://www.aboutdebian.com/dns.htm - How To Set Up Linux DNS Services
http://www.rscott.org/dns/ - DNS Oversimplified
DDNS:
Real Dns 6 6 2 – Dynamic Dns Update Client Duc For Windows
http://www.debianadmin.com/howto-setup-dhcp-server-and-dynamic-dns-with-bind-in-debian.html - Howto setup DHCP Server and Dynamic DNS with BIND in Debian
https://www.debian-administration.org/article/Configuring_Dynamic_DNS__DHCP_on_Debian_Stable - Configuring Dynamic DNS & DHCP on Debian Stable
https://www.debuntu.org/how-to-set-a-lan-gateway-with-dhcp-dynamic-dns-and-iptables-debian-etch/ - How-To: Set up a LAN gateway with DHCP, Dynamic DNS and iptables on Debian Etch
http://www.randombugs.com/linux/linux-isc-dhcp-server-dynamic-dns-updates-debian-ubuntu.html - Linux ISC DHCP Server and Dynamic DNS updates under Debian and Ubuntu
Real Dns 6 6 2 – Dynamic Dns Update Client Linux
Sin city free. CategoryNetworkCategorySoftwareCategorySystemAdministration Reglas de la ruleta.

